Attacking & Defending CI/CD System
Lama Workshop: 2 Hari
Level Workhsop: Beginner-Intermediate
The CI/CD system is an essential tool used daily by organizations to deliver software more quickly through job automation. However, it also becomes a target for attackers due to its centralized nature, containing valuable information such as access credentials and secrets for other systems. The increasing prevalence of attack vectors poses a significant threat, yet many developers are unaware of the security risks associated with these systems, as they primarily focus on delivering the product for customers.
In this workshop, we will cover techniques for attacking CI/CD systems from an attacker's perspective, based on real-world scenarios and we will explore implementing security best practices to defend against unauthorized access to organizational systems.
Who Should Attend?
- Software Engineer / Developer
- Infrastructure / Cloud / DevOps Engineer
- Security / AppSec Engineer
- Penetration Tester
Prerequisites:
- Basic knowledge of Linux system and Command Line Interface (CLI).
- Understanding the basic concepts of container technology and cloud.
- Knowledge of MITRE ATT&CK® Framework and other security frameworks.
Hardware / Software Requirements:
- A laptop with Virtual Machines installed (VirtualBox, VMware).
- Minimum 16GB of RAM and 80GB free storage.
- Stable internet connection (Wifi, Hotspot)
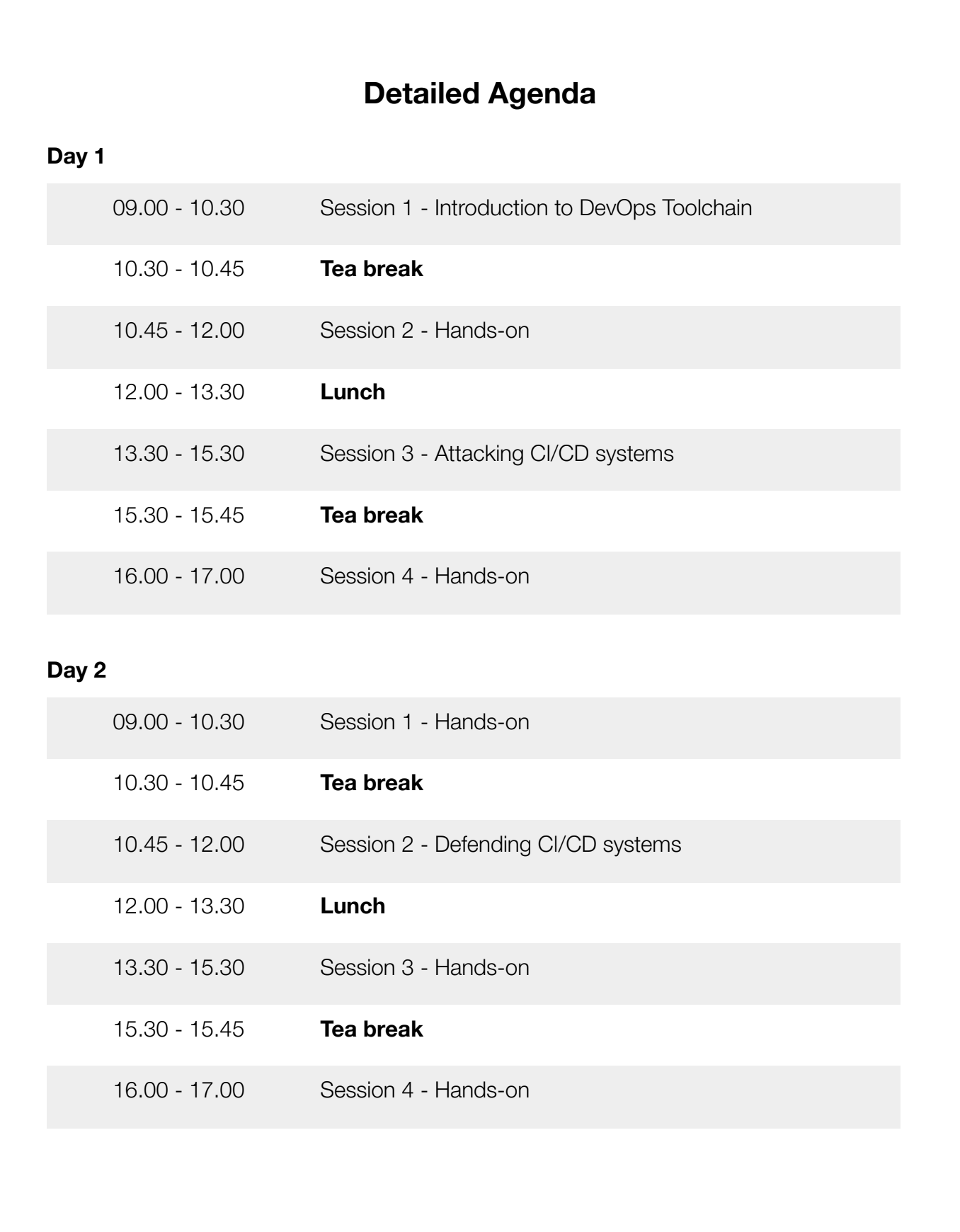
Agenda - Day 1
1. Introduction to CI/CD system
● Introduction to DevOps Toolchain
○ Source Code Management (SCM)
○ Continuous Integration / Continuous Delivery (CI/CD)
○ Container and Orchestration Technology
○ Infrastructure as Code (IaC)
● Deep dive into CI/CD system
○ Understanding CI/CD architecture and components
○ The mechanism behind the runner
○ Self-hosted and managed runner
● Hands-on:
○ Setting up lab environment
2. Attacking CI/CD systems
● Common threats and attack vectors
● Real-world stories of CI/CD attack
● Exploiting weaknesses in CI/CD systems
● Software supply chain attack
● Exfiltrating secrets in CI/CD systems
● Escalating privileges and compromising CI/CD systems
● Abusing CI/CD system to access other systems
● Bypassing mechanism of CI/CD systems
● Managed CI/CD system
○ Identifying the threats and misconfigurations
● Hands-on:
○ Unsecure CI/CD configurations
○ Poisoning CI/CD pipeline
○ Exfiltrate secrets from CI/CD pipeline
○ Multiple ways to escape container
○ Accessing internal system from compromised CI/CD
○ Exploring new attack methods
Agenda - Day 2
3. Defending CI/CD systems
● Compliance and governance of CI/CD systems
● Security standard frameworks
○ NIST
○ NSA/CISA
○ CIS
● Principles of Least Privilege
● Hardening CI/CD Systems
○ Securing the underlying infrastructure
● Implementing Network Security Policy
○ Firewall rules and network segmentation for CI/CD systems
● Logging and Monitoring
○ Detecting Malicious Activity in CI/CD systems
● Hands-on:
○ Auditing the CI/CD systems using security frameworks
○ Preventing tampering attacks using code signing
○ Hardening CI/CD pipeline
■ Container sandboxing with Sysbox
■ Restricting capabilities using AppArmor and Seccomp
○ Detecting malicious activity using runtime security
○ Analyzing attack via logs
He also Holds industry certifications, including the Certified DevSecOps Professional (CDP), Certified Kubernetes Administrator (CKA), and Certified Kubernetes Security Specialist (CKS). Yuga frequently volunteers as a speaker for webinars and industry events and also as a trainer for government and telco companies.